Introduction[]
The Castlecops' Malware Removal and Prevention wiki articles were highly comprehensive, and the SpamWiki staff often referred people there for help. With the shutdown of Castlecops in December 2008, there is a temporary gap that needs to be filled. This article will attempt to address some of the issues as they relate to spamming and the hosting of spamvertised websites.
It's easy to curse the creeps filling our inbox with spam for drugs, watches, and penile enlargement placebos. Why doesn't somebody stop them?
The fact is that there is a huge industry trying to do just that, and many more people doing it as a volunteer effort. The most prolific spammers can't just mail spam from their own computers, because everyone would block any email from their internet addresses (IP addresses). And they can't just host their websites on a commercial hosting service like everyone else, because those services would be under intense pressure to shut their sites down.
"We have met the enemy, and he is us."[]
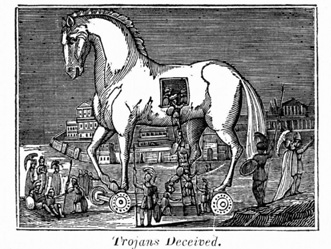
The majority of the spam emails being sent now depend on the use of hijacked computers, infected with malware (bad computer programs) called trojan horse viruses. The name comes from the legend of the Trojan War: After a long seige, the Greeks built a wooden horse and wheeled it to the gates of Troy as as gift. The Trojans voluntarily took it inside their city gates. That night, the Greek soldiers inside emerged, opened the city gates, and allowed the Greek army to take control of the city.
Similarly, victims of malware trojan infections voluntarily accept them onto their computers. Once there, the trojan can disable security software and contact outside computers to download more malicious programs. Those programs allow criminals to use the computer to steal the victim's personal information, like bank account passwords and social security numbers. But they also allow the computer to be used to send spam emails, to host spamvertised websites, or even to stage attacks on businesses or government agencies. (Part of the reason for the demise of Castlecops was the damage from just such an attack.)
So most of the spam you receive depends on the active cooperation of computer owners like yourself. Having internet access entails accepting the responsibility for making sure your computer is not a participant in criminal activity.
Is using the internet too dangerous for the average person?[]
Obviously, the answer is "no" or we wouldn't be making this wiki available on the internet. The volunteers here go to all kinds of dangerous sites, and for the most part we get away with it. But we have educated ourselves about the types of risks involved and follow some simple rules to minimize risks.
Email safety[]
Since delivering a trojan depends on the victims' cooperation, it's not that hard to avoid infection if you are aware of how prevalent such attempts are. Your junk spam filter probably has several attempts arrive on any particular day, and a few will get past into your inbox. But they usually are pretty easy to recognize if you know what to look for. You wouldn't assume a ring you got from a bubble gum machine is a real diamond, and you should have the same level of suspicion when things come to you in unsolicited email. When you get an email that asks you to visit a website or open an attachment, think:
- Who is the sender? Most trojans come from people who don't know your name, and the "from" won't list anyone you know personnally. But it isn't difficult to "spoof" someone else's name in the "from." In fact, if you send emails from home using your business email address in the "from," you've proven how easy it is. People doing it for less legitimate purposes can put any address they want there. Always remember that the "from" address means absolutely nothing.
- Why did that person send me this? 99.99999% of the "secret admirers" sending you stuff will be criminals trying to get you to download malware. (And if your real secret admirer thinks you are so stupid you would download something without knowing who sent it, you can do better.)
- Is this item what it claims to be? The clickable link may say "hallmark.com" but if your email client uses html (shows pictures and allows you to click on links to open web pages), the actual link doesn't have to go to the same place. Don't click on links if you don't have access to the raw text view. Go to the main website for the ecard company by typing it in your browser, then follow their links to your greeting card.
- Where is the email from? Again, it's very useful to look at the raw email with its headers to see if the "from" address goes with the "Received from" lines in the header. If you don't know how to check those things, assume the email could be from an imposter.
Any unsolicited commercial email from a company you have no prior relationship with should be assumed to be from criminals. Don't follow the links, don't give them credit card numbers, don't give them personal information, and don't put anything from them on your computer or in your body.
Decoding fake website URLs[]
Phishers and malware distributors make their links hard to interpret so they can fool you into believing you're visiting a legitimate site. If you're alert enough to check, you can figure them out, though.
For instance, try clicking on this link:
http://bankofamerica.com
Moral of the story: Links are determined by invisible html code and can be attached to any words, phrases or pictures. They can even be attached to the printed web addresses of unrelated websites.
Now look at this URL:
http://logon.bankofamerica.com.3432354.example.com/userlogon.asp?2343243
Many people read as far as "bankofamerica.com" and assume this is a real link to a real bank. But computers don't read left to right the way people do. They read left to right until they see punctuation that tells them what to do, then read backward to get the information they're supposed to use to do it.
- So a computer sees the "http://" and says, "Ok, this is a link to a website."
- Then it reads on until it gets to the "/" It stops and says, "Ok, that was the main location of the website."
- It goes backward and sees ".com" and says, "That's a top level domain name. It is shared among lots of sites. I need to go another step."
- Then it sees "example.com" and says, "example.com" is the domain name of the site I'm looking for. Let me find out where that is."
Notice that it hasn't gotten anywhere close to thinking it's looking for bankofamerica.com. It's going to go looking for "example.com," and then ask for the other information there.
To interpret URLs, try to think like a computer. Look for that first "/" and then work backward to see where it's trying to take you. And remember you have to be looking at the raw html source code, not the visible text, because they can be different. (Ha, ha!)
Recognizing hijacked legitimate sites[]
Usually, once you determine where the URL is taking you, you can get a good idea of whether to trust the site. But many legitimate innocent websites are hijacked by criminals. Often these are sites that are run by community groups and individuals who would normally be trustworthy -- but who often are not spending a lot of time monitoring their websites. If an attacker can guess a password and put malicious files on the site, that site may end up lending its credibility to the criminal.
These links often come from spam emails or website forum/comment spam. That's your clue -- there's no reason a website for a Boy Scout troop in Hoboken should be hosting a file for a site selling Viagra or promising porn videos. Stay away, and if you feel certain the site is innocent, notify the owners of the need to clean their website.
Preventing websites from performing unauthorized actions[]
Surfing the web is fun because websites can do so much. They can show animations, play music, let you play games, all kinds of things. In a perfect world we could sit back and enjoy the experience, blissfully unaware of how much work went into creating those sites.
But allowing many of those functions means giving websites permissions for those sites to make your computer do things you don't understand. That's a risk. No site should be given such permissions without you evaluating its trustworthiness first.
ActiveX[]
ActiveX controls are part of Microsoft's Internet Explorer web browser. They are very powerful and are designed to allow you to enjoy a multimedia experience without having to understand how it is happening. The problem is that all kinds of things can be going on without you knowing anything is happening. Websites can even download and install trojans without you knowing it happened -- something called "drive-by downloads."
The easiest solution is to not use Internet Explorer. If you choose to use it -- you may wish/need to use a trustworthy site which requires ActiveX or which refuses to interact with other browsers -- you need to set up two levels of security. All sites you visit in the Internet Zone should have the security level set to "High." The sites you trust can be added one at a time to the Trusted Zone, which can have medium or low security. But remember the risk of trusted sites becoming hijacked.
Unfortunately, using the high security level on Internet Explorer can lead to a lot of annoying bleeping and popups, so many people quickly disable it.
Other browsers, like Firefox, Seamonkey, Safari, Opera, and Chrome, don't use ActiveX at all.
Javascript[]
Javascript is another programming language that is used by all browsers. It's used for a lot of the basic functions you expect in a website, like submitting comments or making purchases. You can't easily do without it. But it can also be used for malicious activity.
So you need a way to block Javascript by default for websites you're visiting for the first time, but you want it to be easy enough to disable that you aren't tempted to reduce your global security settings. For Mozilla browsers like Firefox and Seamonkey, you can add the Noscript extension. While you may have to allow permissions for multiple entities to view some commercial websites, it still only involves right-clicking a button on your task bar.
Why don't Safari and Opera run Noscript? Probably because they are not used by many people running Microsoft Windows. Most malware is written to infect the greatest number of people, so malware creators don't spend a lot of time creating malware to infect Macs or Linux computers. As far as Google Chrome, it's very new so people are still evaluating its safety, but any add-on that could prevent page ads from being visible would run counter to Google's business interests.
Meta refresh[]
Meta refresh means a website has instructions telling your browser to find another page. When you go to a site that has moved, it uses that type of command to get you automatically to the new page. But when it tells your computer the name of the new page, it can tell it to get a malware program instead of a website page. You would know this is happening when your computer asks you where you want your download stored.
Noscript won't block that. It's important to have your browser set to always ask where to put any downloads, even if you always want them in the same place. That way when it asks, you can click "cancel" and block the download.
Helper applications[]
Programs used to display certain web content like animations/videos, pdf files and even word processing documents may be exploited by malware. Noscript will block a lot of these, too. Only permit them for sites you're willing to trust.
Getting information from WHOIS records[]
Although spammers try to conceal as much real information as possible, there are some things they have to make public. One of the most important is the domain registration information that allows people looking for a website using a name -- like "example.com" -- to find the actual location of that website's internet address (which is actually a number, like "192.168.1.1").
No one can find a secret website, and domain registrations have to go through companies that are authorized to register domain names and which have to follow rules set by their respective registries.
Let's look at the whois for a spammer domain, laraegercakhosts.net. They're spamming for a work-at-home scheme. You can find whois lookups at many sites, one of which is who.is:
Registry Whois Domain Name: laraegercakhosts.net Status: ok
Status "ok" means the domain name has no problems or restrictions. Some restrictions, like "ClientUpdateProhibited" may not mean there is a problem -- it may have been added to reduce the risk that someone will try to steal a domain name. "ClientHold" means the domain cannot function as the name of a website, though it could still be used help other websites function.
Registrar: TUCOWS INC. Whois Server: whois.tucows.com Referral URL: http://domainhelp.opensrs.net
That means Tucows, or one of the "resellers" it works with, dealt with the domain name owner and that they provide information necessary for web browsers to find the site. If a site is fraudulently registered, they must suspend it. Registrars may also have registration agreements that allow them to suspend it for other illegal activity and spamming.
Expiration Date: 2009-12-18 Creation Date: 2008-12-18 Last Update Date: 2008-12-18
This tells you that this domain name didn't exist before December 18, 2008. The spam arrived on December 27. If for some reason you needed to know how legitimate this site is, you would have serious doubts about a site whose domain name was less than two weeks old. A site with a longer history is more likely to have comments posted on the internet from people who have had some experience with that business. (A site you've never heard of with thousands of comments, on the other hand, may have been trying to create its own comments to generate traffic or else is trying to bury any negative comments deep in the search engine results.)
Whois Registrant:
Contactprivacy.com
96 Mowat Ave
Toronto, ON M6K 3M1
CA
Domain name: LARAEGERCAKHOSTS.NET
Administrative Contact:
contactprivacy.com,
96 Mowat Ave
Toronto, ON M6K 3M1
CA
+1.4165385457
Technical Contact:
contactprivacy.com,
96 Mowat Ave
Toronto, ON M6K 3M1
CA
+1.4165385457
Contactprivacy.com is a company that allows people to register websites without making their contact information public. It's a trade-off -- the registrant gets more privacy, but they are in a weak position if they need to prove they own this domain.
Is there some reason a business doesn't want you to know it's real location? In this case it's possible; it could be a home-based business run by a single woman, after all. But the spam did list a street address (as required by US law) and said you could contact them to be unsubscribed from their mailing list. So there's a disconnect.
It would make you wonder if the address in the spam is real, whether contacting them would really get you unsubscribed, and whether the same spammer will be back next week with a brand new domain name, spamming you again, and pretending to have no relationship to this domain name. And since the business not only concealed the address/phone/email but also concealed its actual name, you can conclude they aren't terribly worried whether they still own this domain name five years from now.
Antivirus/antispyware programs[]
Those would seem to be the most obvious protection, and they're certainly essential. But it's important to realize the limitations.
There is always a delay between the first time a new malware program is observed the the time the AV programs' definitions can recognize it. That's the time when it's being mailed out in spams by the millions. (On the other hand, since the trojans' job is mainly just to let other programs enter, it's common for your antivirus to have no objection to a file when you download it, then pitch a fit if you try to run it. But don't count on it.) You have to be smart and suspicious and assume you will encounter lots of copies of malware your antivirus can't recognize yet.
That being said, don't even think about letting your antivirus subscription expire. It could be the only thing that recognizes some new method of drive-by download that affects browsers or other programs that have not previously been targets of attack.
There are a number of free antivirus programs available. Some are the same as the paid versions but with less features, but others are less effective at detecting viruses. Even among paid versions, detection effectiveness varies significantly, and a product's stats can drop if it happens to be less effective against the malware de jour. Shadowserver lists a number of products; if you look at the various links on the left for daily, weekly, monthly, and yearly stats, you will see there is no single product that is consistently "the best."
If you have paid security software already, check to see what it includes. You need antivirus, antispyware, and firewall features. They may or may not be included in a single "security suite" program. For any you don't have, there are free programs available that get the job done. Generally they are for personal use and don't include support except from other users on internet forums. They may lack other features, such as updating themselves or doing systems scans on a schedule instead of manually, so know which tasks you'll be responsible for taking care of yourself.
Some free antivirus programs (again, for personal use):
Free antispyware applications (often users have more than one, but only run one at a time):
Firewall software[]
Windows includes its own firewall. It's designed to stop outsiders attempting to log onto your computer. But it does not affect outgoing traffic. Remember, the trojan was invited in -- it's only the outgoing traffic it creates that is abnormal. An alert from your firewall may be the only clue that you have a trojan trying to contact the mothership or that you have some malware using your computer to send spam.
You can only run one firewall at a time. You must turn off the Windows firewall to install another. Your antivirus program may include one, in which case you should not install another unless you deactivate it. If you do not have a separate firewall, there are a number of good free downloads for personal use, some bundled with AV programs, some bundled with toolbars or other annoying add-ons you may wish to unclick before installing. Be sure whatever you download works with your operating system (Vista, XP, ME, Win98, etc.):
- Comodo Internet Security
- Webroot Desktop Firewall Free
- Online Armor Personal Firewall
- Sygate Personal Firewall Free
- Sunbelt Personal Firewall
- ZoneAlarm Free Firewall
- Last free version of Kerio Free Firewall
- Jetico Personal Firewall v.1
- OutpostPro Firewall
Conclusion[]
Using the internet can be dangerous. So can crossing the street. Learn the risks, take responsibility for yourself and for the other people who your computer could potentially harm.
And don't be the one who insists on seeing the dancing bunnies (Playboy or otherwise).