PublicDomainRegistry aka PDR[]
PublicDomainRegistry' is a registrar in India.
Description of the Registrar[]
PublicDomainRegistry is a global leader in providing Domain Registration Services and is ranked amongst the fastest growing ICANN Accredited Registrars worldwide. Our services are made available through our global network of Partners.
PDR LTD. D/B/A PUBLICDOMAINREGISTRY.COM is a wholly-owned subsidiary of Endurance International Group Holdings, Inc.
Our Corporate Officers:
- Hari Ravichandran, President
- David Bryson, Secretary
- Tivanka Ellawala, Treasurer
- Timothy S. Mathews, Chief Accounting Officer
 Hari Ravichandran |
 David Bryson |
 Tivanka Ellawala |
Anti-Fraud Position[]
Processes for handling abuse complaints for inaccurate whois, spam, fraud are at http://publicdomainregistry.com/process-for-handling-abuse/
Official Position[]
Actual Behavior[]
Registrar responsiveness[]
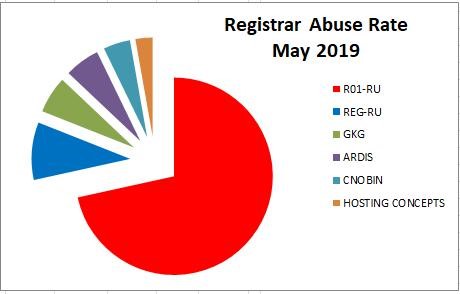
Showing all registrars including R01.RU
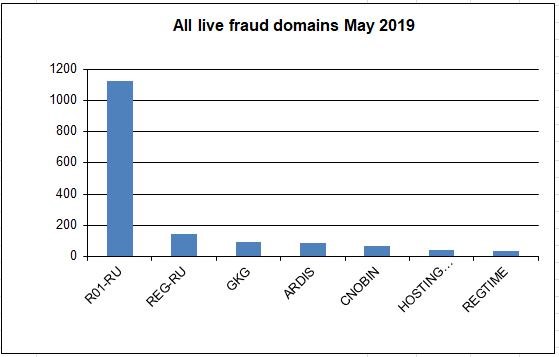
Showing all registrars excluding R01.RU
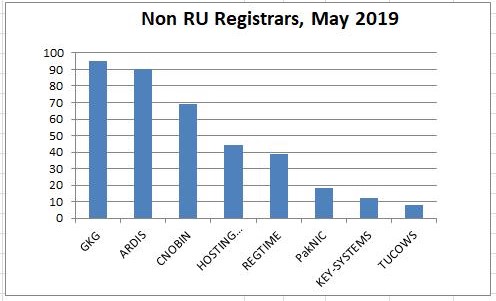
Piechart showing the crime sponsoring contribution by each registrar.
The comparison between this registrar and others can be seen on the graphs.
It shows how many domains have not been suspended by various registrars over the past year. The higher the column, the more domains are sponsored by the registrar.
Currently the most abused registrar is Russia's R01.ru. This registrar sponsors the vast majority (often over 60%) of the fraud domains used within the Eva Pharmacy group.
The second most abused registrar is Russia's REG.RU REG.RU at over 25%
The next most abused registrar is GKG GKG at 4%.
The next most abused registrar is The Netherlands' Hosting Concepts aka OpenProvider at 3%.
These are followed by Russia's ARDIS, India's PublicDomainRegistry PDR, China's CNOBIN, Canada's Tucows, and Pakistan's PakNIC.
Outside of Russia, most registrars have been quick to terminate the service contracts with these cyber-criminals upon seeing the obvious evidence of fraud.
Examples of domains used for fraud[]
These domains were tested on September 16, 2016 and were found to be live. Each heading links to evidence that the domain is being used for fraud.
See also PDR_list
Canadian Neighbor Pharmacy[]
goodmedstrade.click mygenericsmart.link
CanadianPharmacy[]
secureaidshop.link
MyCanadianPharmacy[]
connitheresina.club doloritasjuditha.club
profit-lux[]
profit-lux.com
RxExpressOnline[]
agatheedithe.club ailahelyn.club arliediahann.club aureliebarbabra.club carlinetabbi.club chandadelinda.club clemmyshelby.club corneliajere.club darbieblisse.club delphiniacorissa.club yettahelga.club
RxMeds[]
annisbarrie.club bekkihelyn.club dotevita.club
Toronto Drugstore[]
remedialrxmarket.work
Suspended Domains[]
Canadian Health&Care Mall[]
akiorncx.com (suspended) healingbestmarket.com (suspended)
CanadianPharmacy[]
herbalhotsale.com (suspended) thepillvalue.com (suspended) yourherbsupply.com (suspended)
Men's Health[]
familygenericsshop.com (suspended)
My Canadian Pharmacy[]
genericmedsservice.com
US Drugs[]
theremedymarket.com (suspended)
Common IP addresses[]
A quick way to verify these sites is to examine the hosting addresses. Note that * items have been removed. Many compromised hosts used for this operation during September 2020 - May 2021 were located at these IPs.
| - - - - - - - - - - - | - - - - - - - - - - - | - - - - - - - - - - - | - - - - - - - - - - - | - - - - - - - - - - |
|---|---|---|---|---|
| Live | ||||
| ---- | ||||
| 2.184.67.164 | 5.101.140.77 | 5.188.211.29 | 37.46.135.24 | 51.222.136.197* |
| 51.89.151.227 | 84.15.139.143 | 84.200.77.180 | 95.165.145.236 | 95.165.149.124 |
| 95.165.27.205 | 95.31.40.41 | 103.117.141.163 | 103.121.91.117 | 103.126.6.161 |
| 103.127.31.154* | 103.135.128.72* | 103.139.42.59 | 103.146.23.100 | 103.147.153.123* |
| 103.147.153.126* | 103.157.224.90 | 103.228.114.93 | 103.236.150.106* | 103.236.201.228 |
| 103.92.25.124 | 103.242.117.197 | 103.28.149.174 | 103.30.246.103 | 103.83.192.109 |
| 103.9.158.67 | 103.92.25.124 | 185.182.105.220 | 185.182.105.221 | 185.227.136.203 |
| 185.24.232.98 | 185.227.136.205 | 198.211.33.45 | 200.55.243.166* | 202.145.2.67 |
| Removed | ||||
| ---------- | ||||
| 5.133.12.16* | 5.181.158.179* | 5.181.158.181* | 5.187.52.1* | 5.187.52.12* |
| 5.187.52.13* | 5.187.52.9* | 5.2.89.72* | 5.253.62.111* | 5.45.82.242* |
| 31.132.1.40* | 37.61.211.187* | 37.61.211.188* | 37.61.211.189* | 45.119.41.11* |
| 45.119.41.12* | 45.119.41.14* | 45.125.65.93* | 45.131.83.10* | 45.137.21.144* |
| 45.137.21.166* | 45.67.116.219* | 45.86.163.7* | 51.158.23.140* | 51.210.134.178* |
| 51.38.80.31* | 58.64.137.69* | 62.141.56.196* | 78.157.200.139* | 80.233.134.248* |
| 80.233.134.249* | 81.4.110.230* | 82.199.101.248* | 82.199.101.44* | 82.199.104.3* |
| 85.17.219.96* | 85.183.104.125* | 85.254.72.7 * | 87.120.253.209* | 89.105.221.82* |
| 89.222.128.42* | 91.199.41.51* | 91.199.41.53* | 91.199.41.55* | 93.119.105.5* |
| 94.126.173.105* | 94.152.214.31* | 94.156.175.107* | 101.53.147.97* | 101.99.90.111* |
| 103.108.117.18* | 103.117.141.184* | 103.130.218.113* | 103.138.96.86* | 103.142.25.210* |
| 103.160.144.64* | 103.160.62.153* | 103.221.220.169* | 103.42.58.61* | 103.56.148.90* |
| 103.6.207.162* | 103.8.26.45* | 103.86.51.178* | 103.92.30.110* | 109.232.240.24* |
| 111.90.158.205* | 112.78.10.214* | 119.59.123.55* | 119.59.123.55* | 128.1.60.6* |
| 130.185.72.89* | 134.119.186.27* | 134.119.186.29* | 141.98.10.125* | 141.98.10.136* |
| 141.98.10.142* | 141.98.10.225* | 146.247.49.105* | 146.88.26.167* | 159.148.186.165* |
| 159.148.187.4* | 159.148.187.6* | 167.114.188.36* | 170.130.173.37* | 171.244.143.163* |
| 173.213.80.216* | 176.123.9.67* | 178.239.177.183* | 178.255.40.234* | 179.43.149.28* |
| 180.131.147.100* | 185.105.109.213* | 185.108.128.181* | 185.128.42.106* | 185.128.42.107 * |
| 185.128.43.18* | 185.128.43.21* | 185.128.43.54* | 185.130.206.6* | 185.140.249.133* |
| 185.183.104.123* | 185.216.8.156* | 185.227.136.206* | 185.24.232.118* | 185.24.232.134* |
| 185.24.232.76* | 185.9.158.36* | 185.99.3.68* | 185.99.3.80* | 194.5.179.140* |
| 195.123.247.36* | 198.27.110.97* | 209.127.28.5* | 209.97.184.221* | 212.34.158.134* |
| 212.34.158.134* | 213.226.100.10* |
Where to contact the compromised hosting ISP:
Abuse contact for '5.2.88.0 - 5.2.89.255' is 'alvaro.montero@ipcore.com' Abuse contact for '5.45.80.0 - 5.45.83.255' is 'abuse@ispiria.net' Abuse contact for '5.101.140.64 - 5.101.140.95' is 'abuse@ukservers.com' Abuse contact for '5.181.158.0 - 5.181.158.255' is 'abuse@mivocloud.com' Abuse contact for '5.133.8.0 - 5.133.15.255' is 'abuse@artnet.pl' Abuse contact for '5.187.48.0 - 5.187.55.255' is 'abuse@artnet.pl' Abuse contact for '5.188.211.0 - 5.188.211.255' is 'abuse@pindc.ru' Abuse contact for '5.253.60.0 - 5.253.63.255' is 'abuseto@adminvps.ru' (Removed) Abuse contact for '27.124.80.0 - 27.124.95.255' is 'abuse@medialink.net.id' Abuse contact for '31.200.247.0 - 31.200.247.255' is 'ripe@unelink.com' Abuse contact for '37.46.132.0 - 37.46.135.255' is 'abuse@abusehost.ru' Abuse contact for '45.67.116.0 - 45.67.116.255' is 'abuse@itns.md' Abuse contact for '45.86.163.0 - 45.86.163.255' is 'support@crowncloud.net' Abuse contact for '45.125.65.0 - 45.125.65.255' is 'abuse@tele-asia.net' Abuse contact for '45.131.83.0 - 45.131.83.255' is 'abuse@sered.net' Abuse contact for '51.89.148.0 - 51.89.151.255' is 'abuse@ovh.net' Abuse contact for '79.172.193.0 - 79.172.193.255' is 'abuse@deninet.hu' (Removed) Abuse contact for '80.233.134.0 - 80.233.134.255' is 'abuse@telia.lv' Abuse contact for '82.199.104.0 - 82.199.107.254' is 'abuse@seven-sky.net' Abuse contact for '84.15.136.0 - 84.15.143.255' is 'abuse@bi.lt' Abuse contact for '84.200.77.0 - 84.200.77.255' is 'abuse@accelerated.de' (Removed) Abuse contact for '85.254.72.0 - 85.254.72.255' is 'support@serveria.com' Abuse contact for '87.120.253.0 - 87.120.253.255' is 'abuse@neterra.net' Abuse contact for '89.105.192.0 - 89.105.223.255' is 'abusedesk@novoserve.com' Abuse contact for '89.222.128.0 - 89.222.131.255' is 'abuse@netorn.net' 'abuse@netorn.ru' Abuse contact for '80.233.134.0 - 80.233.134.255' is 'abuse@telia.lv' Abuse contact for '93.119.104.0 - 93.119.105.255' is 'abuse@virtono.com' Abuse contact for '94.152.0.0 - 94.152.255.255' is 'abuse@kei.pl' Abuse contact for '94.156.175.0 - 94.156.175.255' is 'abuse@iws.co' Abuse contact for '95.24.0.0 - 95.31.255.255' is 'abuse-b2b@beeline.ru' Abuse contact for '95.84.128.0 - 95.84.159.255' is 'abuse@rt.ru' Abuse contact for '95.165.128.0 - 95.165.255.255' is 'abuse@spd-mgts.ru' Abuse contact for '103.6.204.0 - 103.6.207.255' is 'yogie@redwhite.co.id' Abuse contact for '103.9.156.0 - 103.9.159.255' is 'cuong.trinh@vnso.vn' Abuse contact for '103.28.148.0 - 103.28.149.255' is 'support@easyway.co.id' Abuse contact for '103.56.148.0 - 103.56.149.255' is 'abuse@jagoanhosting.com' Abuse contact for '103.86.48.0 - 103.86.48.255' is 'abuse@bangmodhosting.com' Abuse contact for '103.92.24.0 - 103.92.27.255' is 'hm-changed@vnnic.vn' 'system@tlsoft.vn' Abuse contact for '103.117.141.0 - 103.117.141.255' is 'abuse@casbay.com' Abuse contact for '103.121.88.0 - 103.121.91.255' is 'tampd@bkns.vn' Abuse contact for '103.126.6.0 - 103.126.7.255' is 'shazim@serverstack.in' Abuse contact for '103.138.96.0 - 103.138.96.255' is 'hello@hostitsmart.in' Abuse contact for '103.146.22.0 - 103.146.23.255' is 'duc@lanit.com.vn' Abuse contact for '103.147.152.0 - 103.147.153.255' is 'abuse@shineservers.com' Abuse contact for '103.221.220.0 - 103.221.223.255' is 'hoanglong@azdigi.com' Abuse contact for '103.236.201.0 - 103.236.201.255' is 'admin@idcloudhost.com' Abuse contact for '111.90.128.0 - 111.90.159.255' is 'abuse@shinjiru.com.my' Abuse contact for '112.78.0.0 - 112.78.15.255' is 'vanht@ods.vn' Abuse contact for '130.185.72.0 - 130.185.72.255' is 'report@parspack.com' Abuse contact for '119.59.96.0 - 119.59.127.255' is 'abuse@metrabyte.cloud' Abuse contact for '141.98.10.0 - 141.98.10.255' is 'admin@serveroffer.lt' Abuse contact for '146.247.49.0 - 146.247.49.255' is 'abuse@netcetera.co.uk' Abuse contact for '159.148.186.0 - 159.148.186.255' is 'support@serveria.com' Abuse contact for '159.148.0.0 - 159.148.255.255' is 'abuse@latnet.eu' Abuse contact for '171.224.0.0 - 171.255.255.255' is 'hm-changed@vnnic.vn' 'soc@viettel.com.vn' Abuse contact for '176.123.0.0 - 176.123.11.255' is 'abuse@alexhost.com' Abuse contact for '178.239.176.0 - 178.239.177.255' is 'abuse@irideos.it' Abuse contact for '178.255.40.232 - 178.255.40.235' is 'abuse@artnet.pl' Abuse contact for '179.43.149.0/26' is 'support@privatelayer.com' Abuse contact for '180.131.144.0 - 180.131.147.255' is 'abuse@nawala.org' Abuse contact for '185.24.232.0 - 185.24.232.255' is 'abuse@servebyte.com' Abuse contact for '185.128.40.0 - 185.128.43.255' is 'abuse@rackend.net' Abuse contact for '185.130.206.0 - 185.130.207.255' is 'abuse@as61317.net' Abuse contact for '185.140.248.0 - 185.140.249.255' is 'contact@buzinessware.com' Abuse contact for '185.183.104.0 - 185.183.104.255' is 'abuse@m247.ro' Abuse contact for '194.5.176.0 - 194.5.179.255' is 'berbid238@gmail.com' Abuse contact for '200.55.243.166' is 'radhios@gmail.com' syt.com web page Abuse contact for '202.145.0.0 - 202.145.3.255' is 'abuse@uninet.net.id' Abuse contact for '209.127.0.0 - 209.127.138.255' is 'abuse@servermania.com'
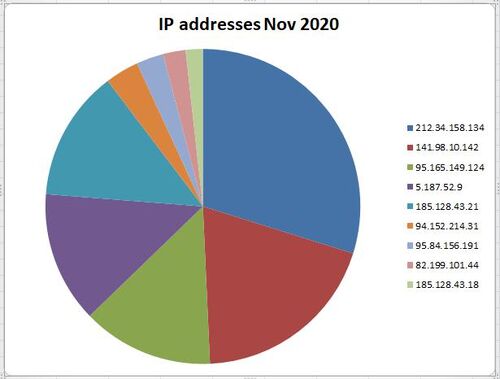
Example of the highest used IP addresses from November 2020
Where to send abuse complaints[]
PDR Ltd. d/b/a PublicDomainRegistry.com Directiplex, Mogra Village Nagardas Road, Andheri (East) Mumbai Maharashtra 400069 India +1 2013775952 tldadmin@directi.com abuse.manager@publicdomainregistry.com abuse@publicdomainregistry.com
Web site http://publicdomainregistry.com/process-for-handling-abuse/
Additional Contact Information[]
Postal address[]
Directiplex, Mogra Village Nagardas Road, Andheri (East) Mumbai Maharashtra 400069 India
Telephone and FAX[]
Phone: +1 2013775952
Related information[]
Pharmacy fraud operations
- Canadian_Health&Care_Mall
- Canadian_Neighbor_Pharmacy
- My_Canadian_Pharmacy
- Toronto_Drug_Store
- Canadian_Family_Pharmacy
- WikiPharmacy
- International_Legal_RX
- US_Drugs
- Men Health
- RxMedications
- RxExpressOnline
- OEM Software
Affiliate program coordinator employing spammers