Description
My Canadian Pharmacy (referred to in this document as MCP) is a longstanding Russian or possibly Ukrainian spam operation which has been relentlessly spamming email users around the world since at least the spring of 2004. The operators are currently wanted by numerous international law enforcement groups including Interpol and the FBI. They largely appear to be tied to credit card fraud and identity theft.
Numerous pharmacy oversight organizations have fielded several thousand complaints per year regarding this illegal operation. They and numerous law enforcement agencies continue to investigate as much as possible regarding the spamming, website setup, DNS setup and (alleged) order processing of this spam gang. This investigation is ongoing.
Spamhaus claims that this group of websites (and their other web operations including International Legal RX and US Drugs) may be linked to the illegal spam group Yambo Financials, who they allege also have direct ties to Alex Polyakov. Polyakov and Yambo each hold places on the Spamhaus Register of Known Spam Operations (ROKSO) database's "Top Ten Worst ROKSO Spammers" list. Subsequent research has uncovered that this spam-promoted property was actually a part of the affiliate program known as "Bulker.biz", whose public forum was at bulkerforum.biz prior to being shut down. Knujon and other groups now consider it part of the Eva Pharmacy affiliate program.
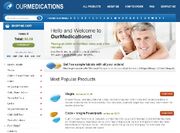
In 2013 it started to appear under a new skin, branded as OurMeds or OurMedications.
Basic Summary
My Canadian Pharmacy is part of an umbrella group of websites which purport to offer discounted pharmaceuticals to an unwitting public. They are notable in that most of their claims are 100% false. They lie in the spam messages they send, they lie in telling you their site is secure, they lie when they say your order is on its way. Even the name itself - "My Canadian Pharmacy" - is a fallacy. No known connection to the country of Canada is present in anything this group has done.
Sample Spam
Subject: Order all medications you need online. Our drugstore is serving your needs for the best quality medications. Canadian Pharmacy offers very low prices comparing with other online drugstores and an excellent service. Trust us when you choose an online drugstore. oju http://profiles.yahoo.com/blog/5PNRBXKO3PU3HHJV3F6HXMVLOI
(The yahoo blog links to hvacwezgiz.com. This is part of a recent deluge of spams using Yahoo Blogs as spammed links to avoid having the real domain names picked up by spam blocklists.)
Your history shows that your last order is ready for refilling. To finish your reorder visit http:(domain deleted by Spamwiki Admin) Please visit the site to complete your order. Because you have ordered from us previously, your prescription is pre-approved. Thank you, Abigail Reese Customer Services
We’ve got a huge variety of choice among all categories of high-quality medication - Men’s Health, Antidepressants, Pain Relievers, General Health, Weight Loss, etc. The products of Canadian pharmaceutical industry are not less qualitative than the American medications. They are just cheaper – that’s the point. Purchase your meds from CanadianPharmacy and save large with our weekly specials and discount offers. Our prices and quality are the best on the Web. (domain deleted by Spamwiki Admin) Instant shipping worldwide. CONFIDENTIAL purchase.
Speaking about e-shops, CanadianPharmacy drugstore is the most trustworthy online drugstore that has gained a reputation of providing with the top quality medications at the absolutely low cost. (domain deleted by Spamwiki Admin) Nobody will know that you are using Viagra because all purchases are TOTALLY CONFIDENTIAL AND SECURE.
 |
 |
 |
 |
 |
 |
 |
Description of Operations
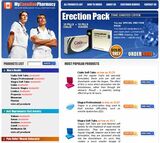
The front page of an MCP website
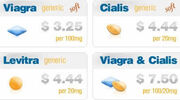
The MCP site is a generic pharmaceutical e-commerce site. They claim to offer generic versions of several prescription drugs including Viagra and Cialis. (Neither of those drugs has a generic version, since as of this writing they are still protected by international patents, but we'll get to that in a bit.)
The site itself features 34 pharmaceutical products in a variety of quantities. They claim to offer these at a substantial discount from traditional American pharmacies (their name is, after all, "My Canadian Pharmacy"). As one example: "Generic" Viagra [Sildenafil Citrate] sells on their site at a price of $2.00 - $3.50 per 100mg pill, dependent on quantity. (That's actually a decrease from their previous price list, but since there the are only selling placebo anyway, it's not like it's a bargain at any price.) Actual Viagra sells for $15 - $16.00 per tablet dependent on quantity (prices gathered from drugstore.com, an actual certified online pharmacy website.) So this would represent a saving of up to 87% per tablet if they were actually selling a real product.
The process of ordering the drugs themselves can take as little as three minutes, and is only limited by how fast the customer can type it in. That's actually a bad thing. There are no surveys to fill out, no prescription or patient data to provide. The consumer merely selects a product, chooses a quantity, checks out, fills in their shipping and credit card data, and submits the order. There is no physician or pharmacist to determine whether the drug ordered would be medically appropriate for the customer. At some point later on, it is assumed, the order will be fulfilled, a confirmation email sent, and the products shipped to the consumer.
Their "How To Order" page outlines this series of steps and makes the claim that "All orders are received via a secure server, to ensure that your sensitive information is kept private and to guarantee you peace of mind."
Operator Identification
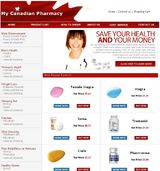
April 2008 site

April 2008 trailer
The spammers behind this group were originally referred to as being part of "Yambo Financials" (by Spamhaus) and are well-documented in the Spamhaus Rokso database. As mentioned above, further research has shown that Bulker.biz are the ones behind this operation, and are also the ones who created and continue to implement their botnet hosting platform (described in more detail below.)
The very broad grouping known as Yambo (which may or may not have links to bulker.biz) has links to credit card fraud, identity theft, and the creation and distribution of child pornography. They are alleged to have originated in either Russia or Ukraine, and their current exact whereabouts are unknown. Yambo also has ties to several major career spammers, including Alex Polyakov. Again, it is cannot be determined at this time whether "Alex Polyakov" has any direct ties to bulker.biz or My Canadian Pharmacy. This is merely the connection which has been made by Spamhaus, based on their internal evidence and research.
Domain Registration Information
While MCP and other Bulker.biz sites formerly used known false aliases and addresses to register their domains (e.g., "Icek Pankovich" and "Pazek Terkovic"), of late (2006 - present) they have taken to identity theft. By using real victims' personal information, it is more time consuming for registrars processing thousands of new registrations to spot the Bulker.biz domains. A survey of Bulker.biz domain registrations documents the extent and consistency of the fraudulent activity: Fake bulker.biz/yambo whois
In at least some instances, a victim's financial information was also stolen to pay for the registration. Anyone who finds their personal information used in the registration information of a spam website should review the Whois identity theft information article.
In 2014 the method changed from using stolen identities, to using a fake name generator service, such as the one found at http://www.fakenamegenerator.com. These fake ID sites will generate real looking names, addresses, phone numbers and credit cards to simulate real identities. The aim is to make it more difficult for registrars to identify fake registrant data. Only the email address will be true, so that the registrant can handle information requests from the registrars.
Website Claims
MCP sites make several fictitious claims, all of which we will examine below.
The "How to Order" page
"Placing an order on Pharmacy only takes a few minutes - less time than it takes to drive to your local pharmacy! We work hard to make your life easy."
This claim is true, but virtually meaningless. Placing an example order (using a control credit card number for tracking purposes) on average it can take less than a minute to order any of the dozens of product types alleged to be available on these sites. It's possible to take even less time. The only hindrance is how fast the user can type.
"All orders are received via a secure server, to ensure that your sensitive information is kept private and to guarantee you peace of mind."
This is patently false.
At no point in the ordering process is a secure page presented to the consumer. One can test this with any of the MCP sites (while they remain alive; they rotate all of their hundreds of domains every three days or less since they don't want to leave any tracks.)
Here is an MCP URL from January 2008 (which remains active and was apparently even renewed by the registrar, AIT Domains, despite having being originally paid with a stolen credit card number):
- http://my-canadianpharmacy.info/
If you select a product (Viagra Soft Tabs), choose a quantity (60 pills) and "check out", you're presented with the following URL:
- http://my-canadianpharmacy.info/cart/checkout/
Notice that there is no SSL formatting for this URL (https:// should appear instead of http://.) This would be standard on any legitimate secure website. But let's test that further by attempting to view that page using a standard SSL URL format:
- Try a secure connection - https://my-canadianpharmacy.info/cart/checkout/
We get
my-canadianpharmacy.info uses an invalid security certificate. The certificate is not trusted because it is self-signed. The certificate is only valid for scan4you.biz The certificate expired on 6/17/2011 9:21 PM. The current time is 4/8/2014 11:32 PM.
That means, their claim "All orders are received via a secure server" is completely false. They are lying to their customers.
Their So-Called "Supporters"
Next we can examine their so-called "supporters" listed at the bottom of the main page.
Pharmacy Checker
HISTORICAL INFORMATION
They feature a logo for Pharmacy Checker (actually located at http://www.pharmacychecker.com) and that logo linked to a locally-hosted page:
- http://gauserrimer.com/index.php?page=pchecker&interface=no
That page was obviously NOT created by anyone at Pharmacy Checker. It claims: "PharmacyChecker has verified that Pharmacy fills orders with a licensed pharmacy in the Canada."
In May of 2006, Gabriel Levitt, the Vice President of Pharmacy Checker, was contacted regarding MCP. Here's what he had to say about the company:
Have you found many people complaining that this group has stolen credit card numbers, and used them? This is of major interest to the FBI. Spamming is bad but they're more interested in credit card theft. To this day I still don't know if they actually ship medication or not. I can look back at past emails on this issue. Also, have you made a formal complaint with this U.S. government about the company? We have filed a complaint with IC3 http://www.ic3.gov/. Take a look at this site.
This is only the first of several logos listed across the bottom, and very obviously its claim is completely untrue.
CURRENT SITUATION
After the fake nature of these logos has been exposed, the links have been deactivated. The counterfeit logos are there, but there is no change to the display if you click on them.
The Better Business Bureau
Again this logo should normally link to a popup window hosted at the BBB. The logo makes the claim "Listed at Better Business Bureau". As it happens, they actually are. However it is not for the reasons they want you to think.
BBB is well aware of My Canadian Pharmacy and has received so many complaints that they actually emphatically do not recommend these sites at all.
The following alert has been issued by the Better Business Bureau:
Based on BBB files, this company has an unsatisfactory record with the Bureau due to its failure to discontinue the use of the BBB's federally registered trademark when demands have been made to do so.
Verified by Visa:
- http://gauserrimer.com/index.php?page=visa&interface=no
Again: this should link to a page featuring copy from the actual Visa website. They describe a process which absolutely does not take place on any MCP website - the handoff to Visa for thorough verification of the merchant and the credit card being processed. Legitimate e-commerce sites like Amazon.com do perform this third party verification. MCP does not do this.
Contacting Visa regarding this misuse of their branding, we received a reply implying that they have no control over how third party websites use their logo:
...the fact that a merchant displays the Visa logo or uses it on a Visa sales draft, does not indicate that Visa endorses the merchant, nor does it guarantee the quality of goods or services purchased from the merchant.
This calls into question the entire branding strategy of the Verified by Visa program. If literally anyone can feature such a link without fear of repercussions from a company such as Visa, how strong is the protection of that brand against fraudulent misuse such as this?
Subsequent requests for details on Visa policy regarding the use of their logos and investigation of illicit e-commerce companies have resulted in no reply whatsoever. No official statement has ever been released by Visa regarding this abuse of their trademarks and services.
Verisign
HISTORICALLY: a locally-hosted page. It featured a Verisign logo and the phrase "Verisign Secure Site".
CURRENTLY
Unfortunately there is no way to verify that this company ever had a certificate with Verisign. The easiest way of course is to see if they even use a secure server by using "https://" instead of "http://" Of course this fails for all My Canadian Pharmacy websites. Several abuse reports have been posted to Verisign regarding this claim, but no answer has ever been forthcoming. It is probably safe to assume they are well aware of these sites.
Canadian International Pharmacy Association (CIPA)
HISTORICALLY The locally-hosted popup window featured the following:
Valid Member: Certified Member Organization: Pharmacy Licence #: 91959 Location: Toronto, Canada Current Status: Active The only domain authorized for this CIPA Seal is: My Canadian Pharmacy
CURRENTLY
Representatives from CIPA [1] were contacted regarding this claim, and they responded by saying that no such company (My Canadian Pharmacy) is listed in their records, nor has any such company ever been approved by CIPA. The so-called "Licence #" is not only fictitious, it's not even in the right format for their registration numbers. They don't offer "licences" to pharmacies. They merely approve or disapprove of existing pharmacies.
Supporters: Conclusion
In conclusion: not one word of the so-called "endorsements" on these sites have turned out to be true. Their licence is fake, and their claim of offering secure processing of customer data is a lie.
How much would you trust their products?
Their alleged postal address
HISTORICAL
On every MCP website was a footer image claiming their address to be "1592 Wilson Ave., Toronto, ON M3L 1A6".
The details of the address varied occasionally, sometimes claiming to be located in Don Mills, ON instead of Toronto. They also included this address on their so-called "License" file (more on that in a moment.)
They also feature images of a large corporate building on their websites:

|

|
If you look carefully on the larger one, you can see that they have photoshopped the business name onto the building.
Here's what 1592 Wilson Ave. actually looks like:
 The actual location of 1592 Wilson Ave., Toronto, ON |
The Better Business Bureau has listed that address as fake / unreachable. It is extremely obvious that they're lying about their real geographic location.
July 2009 update With the appearance of the "My New Canadian Pharmacy" site appearances, they also slightly varied their addresses on their contact page:
Main Office (Headquarters): My Canadian Pharmacy Corp. 7963 17 Avenue, Montreal, QC, H1Z 3R2, Canada ICS International Certified Stocks: Pharmacy Corp. A-58, Prashant Vihar, New Delhi, 110086, India International Orders: My Canadian Pharmacy Int. 120 Eglinton Ave E, Toronto, ON, M4P 1E2, Canada
CURRENTLY
Currently they display on the Contact Us page, a model standing in front of a building (shown above) with the company name obviously photoshopped onto it. At the bottom of the page they display the Montreal false address and non-existent license
http://my-canadian-pharmacy.com/contacts/
7963 17 Avenue, Montreal has no building like the one depicted in their photoshopped pictures.
The actual building nearest to that address is the Mini Entrepol Stor-Wel building. Click it to expand the image.

Their Alleged Owners and Operators
On their "About Us" page they feature a timeline of this so-called company. It would make for some hilarious reading were they not dealing with real people's lives here.
On the page, they claim that Jack Poppins and Carl Rose conceived the company in 1999, and someone named "Paul Newman" joined them in 2000. (Newman is listed as a psychiatrist in the article, but is inexplicably also in charge of logistics, wholesaling and PR.)
Dr. Jack Poppins studied reanimatology at Ontario Medical State University in 1969. He worked as a reanimator in the private clinic, White Ribbon, in Ontario until 1990. He became one of the founders of the famous Jack Poppins clinic, specializing in brain surgery in 1991. In 1992, he completed his Ph.D. on Alzheimer’s disease. He is one of the founders of CIPA (Canadian International Pharmacy Association). Over the years, Dr. Poppins has been an Associate Professor of Emergency Medicine at the University of British Columbia, Director of Professional Programs for the Justice Institute of British Columbia [Parametic Academy], and has also been involved in many Phase 3 studies looking at the safety and therapeutic effects of a variety of medications and therapies. He is married and has two sons. Dr. Paul Newman graduated from the faculty of psychiatry at the University of Ottawa, Ontario in 1973 and started practicing as a family psychiatrist. He practiced psychiatry medicine for 16 years, and since 1992 he has been wasco-owner of several ambulatory medical and travel clinics. In 2000-2001 he and his partner, Dr. Poppins, founded My Canadian Pharmacy and opened the first office in Canada. This opening created national media attention on both sides of the border. He was a founding member of CIPA [Canadian International Pharmacy Association], an organization that represents and supports the ethical and professional practice of international pharmacies. Dr. Newman is also involved in research as principal investigator for a variety of Phase 3 vaccine trials.
"Reanimation" of course, means bringing people back from the dead. That leads to some interesting questions:
- If a university has had an entire program devoted to training reanimators since the 1960's, why haven't you heard of any specialists in the field other than Jack Poppins?
- What is going on in the White Ribbon Clinic that they need to employ such a person full time?
- How did he manage to change his specialty to brain surgery with just a year's additional traininga? (and why would anyone allow a reanimator access to his brain?)
You can almost imagine the spammers sitting around making this up, laughing at the people who will read this and not understand how absurd it is. But if you're willing to pay for and swallow the pills these guys are selling, maybe you would let a reanimator have your brain.
These specific images are thought to be stock photos from the website inmagine.com dating back to 1998. They don't appear on that website anymore. No comment has been forthcoming from InMagine to date.
Each of the image headers on every My Canadian Pharmacy site is actually a stock image from a company called "StockByte". Here are some example stock photo locations for most of the site's image headers:
- http://www.fotosearch.com/SBY854/stk121039rke = Main Index
- http://www.fotosearch.com/SBY854/stk100588cor = How To Order
- http://www.fotosearch.com/SBY128/stk24442med = About Us
Several of these images are included in a collection StockByte has created called "Life Savers":
http://www.fotosearch.com/stockbyte/life-savers/SBY192
Here's more of the same models from that shoot, two of whom appear on the main page image:
- http://www.fotosearch.com/SBY854/stk121021rke
- http://www.fotosearch.com/SBY854/stk121044rke
- http://www.fotosearch.com/SBY854/stk121033rke
The source of the photos of the so-called "doctors" who started My Canadian Pharmacy have yet to be found but appear to be part of the same series in terms of their lighting, composition and poses. As mentioned they may be from a different stock image library. The original stock photos have been used by other websites:
- http://lostpedia.wikia.com/wiki/Hanso_Foundation_facilities
- http://www.vtonuse.ru/
- http://www.aska.com.ua/m1/ru/protection/private/health/index
As an aside, StockByte, the company that owns the images, is now part of gettyimages.com. The photographer is George Doyle.
Performing a google search on these names will only ever lead the user to more research on these fictitious names. Several websites - including that of the Better Business Bureau - have performed similar investigations.
Their So-Called "License"
They claim that in 2001 they registered the company and it received a "drug-selling license."

The license file, present on all MCP sites.
Here's a breakdown of the lies this "licence" tells:
1) Certificate claims to be from the "state" of Ontario, yet also claims to be a Canadian certificate. (Canada does not have states. It has provinces.)
2) The certificate features a fairly generic "seal" with the letters "QC" in the center and the words "The Quality Connection / A Commitment To Excellence" around the perimeter. No pharmaceutical document anywhere in North America features these words. Nor does any legitimate pharmaceutical organization feature these phrases. This also bears a product number in the corner of "OSP 96 12401." I could find no such product anywhere online but I'm keeping my eyes peeled at any Office Depot (for example.) No real certificate is created with product catalog numbers intact. Additionally: The term "The Quality Connection / A Commitment To Excellence" somehow relates to electrical unions. Several Google searches turn up a variety of reports and / or public statements on behalf of American electrical unions who use that complete term as their slogan or motto.
3) Background fake watermark features the words "Ontario County". There is no such location in Canada. (Though there is in New York, US.) Interestingly, there used to be an Ontario county in the province of Ontario until it was adsorbed into the Regional Municipality of Durham in 1972.
4) Features the address "1592 Wilson Ave., Toronto, ON M3L 1A6." The Better Business Bureau has listed that address as fake / unreachable. In September of 2006 I was sent the photograph (shown above) of the genuine location. As you can see, the location is a Subway restaurant located in what appears to be a rather dingy strip mall.
5) M3L 1A6 is a valid postal code, but not for that address. It seems to link up to the beer store at 1718 Wilson Avenue, somewhat further north.
6) Features a License number of "02838940." The Ontario College of Pharmacies does not use this method for identifying their licenses.
7) The "Signature of Issuer" is for one "Eryl Roberts." According to the Ontario College of Pharmacies, no issuer of their certificates has ever had this name. (It's a Welsh name and quite rare, they would likely remember if someone actually did have that name.)
8) The license claims to be issued on July 10th, 2002 and claims to expire on July 10th, 2012. According to the Ontario College of Pharmacies (and I called to make sure) legitimate pharmacy licenses are only issued for a maximum of 4 years, after which they must be renewed. (Interesting: this "license" was so fake as to cause big showbusiness laughs on the phonecall.)
9) The "license" claims to be issued "in accordance with the provisions of Division 104, Chapter 6, Article 6, of the Ontario Health and Safety Code." There are numerous problems with this statement.
- There is no "code", there is, however, an "act".
- That act does not contain any "divisions"
10) (This one is sort of iffy but is the one which relates most closely to this certificate's claims.)
Ironically, the govt. of California appears to have a related "code". Division 104 is briefly listed here:
http://www.arb.ca.gov/bluebook/bb04/headiv/hea_div_104.htm
It covers "Environmental Health", which includes toxic waste issues among numerous others. Why is a pharmaceutical certificate in any way related or involved with this code? (if it indeed is based on it, which as we can see is highly doubtful.)
There is no chapter 6 in the California code, so there could not also be an Article 6. [And let's remember: this is for California, in the US, not Ontario, Canada.]
A better outline is here:
http://caselaw.lp.findlaw.com/cacodes/hsc/1-28.html
However: no "division 104" appears to exist. It is also a thrilling read. ;)
11) Ontario's Health and Safety Act has absolutely no bearing whatsoever on the licensing of the sale of pharmaceuticals. It's a labor act, not a medical one.
http://www.e-laws.gov.on.ca/DBLaws/Statutes/English/90o01_e.htm
12) The "license" claims [in a rather bizarre fashion] that "The license (sic) is required by law to immediately notify the Department of Health Services of any change in the information reported in the Application." Whoever typed this must have meant to use the word "licensee", not "license". (No document can actively notify anyone of anything.)
13) Ontario has no "Department of Health Services", they do, however, have a Ministry.
14) The Ministry is not the government branch which awards licenses to Pharmacists. That would be the Ontario College of Pharmacies [see numerous points above.]
15) The address mentioned above is indeed in an industrial office zone, and it's ironically quite close by several clients I work with regularly. They know this building to not be zoned for medical or retail purposes. Nor is it zoned for wholesale purposes. So either the issuer of the license (we know it's fake but let's play along) was unaware that this was not a medically licensed location, or they did and are in violation of several commerce bylaws.
16) Ontario pharmacists have specific clean-room requirements. No industrial or wholesale-zoned business would ever house a pharmacy that met such requirements while still being surrounded by other industrial compounds. Such a facility would never knowingly be approved by any pharmaceutical authority.
17) There is no "Food and Drug Branch" of any ministry in any province in Canada, never mind Ontario. Nor is the word "food" ever used in relation with anything to do with the licensing or reselling of pharmaceutical products. The US does, however, feature a "Food and Drug administration."
In short: not one single word of this operation's websites, or images, or "Licenses" are valid or truthful in any way. We will see in subsequent data that this tendency towards fallacy extends into the domains they register and the contact information they provide.
The Danger of Illegal Pharmaceuticals
In a report on the Canadian investigative TV show MarketPlace, reporters investigated only one of a series of "rogue" online pharmacies, attempting to discover where their drugs came from, and what quality the drugs they received turned out to be. Their results were compelling.
A transcript may be found here:
In a very small nutshell it uncovered the following:
- Rogue pharmacies tend to feature either no pharmacist on duty whatsoever, or a pharmacist operating illegally.
- In one case a pharmacist in Rhode Island was rubberstamping requests for pharmaceuticals without ever reading any patient information or meeting or having any prior relationship with any of the site's patients at all.
- Drugs received were either expired, placebos (fake), or of questionable contents. Those that actually did feature the ingredients advertised did so in extremely low quantities.
- Most of the drugs received were not manufactured by legitimate pill laboratories. Several came from underground labs in China and posed a serious health risk.
- Pills were always shipped inappropriately. One shipment of Viagra arrived in a loosely packed paper bag inside an envelope. Several broken tablets were found inside. This could pose a serious health risk to a pregnant woman, for example, whose baby would suffer life-long physical defects.
- Pills were approved for sale and shipped in quantities that are generally considered unsafe. For example, commenting on a shipment of Phentermine, pharmacist Helena Decyk said:
"It's actually addictive. With this type of drug there's a tremendous potential for abuse. Now that's a huge amount. Ninety capsules -- that would be enough for three months. Typically this type of medication is indicated to be used for two weeks. Using it longer than two weeks is not recommended by the manufacturer."
Again: this is a rather obvious health risk to the public.
One of the long-standing problems with rogue online pharmacies is that consumers who purchase from them are often too embarrassed to complain about any wrongdoing which the site is responsible for. An elderly man ordering Viagra is not likely to publicly complain because his order of the drug was ineffective. This is something the operators of MCP are probably banking on. That and the fact that they leave absolutely no trail of evidence to identify who the owners and operators are.
The health risks posed by these sites cannot be ignored, which is one of the leading reasons my colleagues and I have decided to investigate and expose these sites for the internationally illegal scam that they are.
Who Is Behind MCP?
Following an initial investigation into this pharmacy in the fall of 2005 employing Usenet newsgroups and several independently investigative websites, as well as anecdotal discussions with members of the pharmaceutical industry, it immediately became clear that these sites were operated by major-league spammers, possibly associated with organized crime.
The Spamhaus website [www.spamhaus.org] lists My Canadian Pharmacy in their Register of Known Spam Operations, aka "ROKSO":
That report, which is a reduced version of an independent report posted here:
Associates the sites with an organization called "Yambo Financials". Yambo is also listed in ROKSO:
The first line of the report on Yambo is troubling:
Huge spamhaus tied into billing for child/animal/incest-porn spamming, pirated software spamming, credit-card "collection" sites.
That definitely corresponds with Mr. Levitt's responses regarding credit card fraud above.
Further in, in point form, we find the following:
Frequently tied to involvement in hijacking ownership of various ARIN netblocks from the rightful owners.
We'll cover this in the next section: Investigating MCP's Technical Infrastructure. While they aren't hijacking ARIN netblocks any more, they're certainly still in the hijacking business.
Finally this segment, which leads higher up the Spammer food chain:
The players are mostly Ukrainian and/or Russian, living in and around Seattle, WA and Gainesville, FL in the USA and in Russia/Ukraine. Also have ties in Paris, France. Have ties to "Alex Blood", who ties to the RegPay child-porn spammers.
Alex Blood, also known as Alexander Mosh, AlekseyB, and finally Alex Polyakov.
As of this writing, Alex Blood was listed as the number one spammer in the ROKSO database. He sounds like a real charmer:
His crimes include:
- "Owning" and operating an illegal botnet numbering in the thousands of hijacked PC's around the world.
- Involvement and possible ownership and operation of a large child porn ring
- Specifically linked to the "regpay" child porn ring
- May potentially be "pharmamaster", a cracker / spammer who was responsible for attacking and eventually shutting down Blue Security, an anti-spam organization, in May of 2006. Also responsible for numerous distributed denial-of-service attacks (DDOS attacks) against several large-scale legitimate websites including Tucows, Blogger.com and Prolexic.
After reading these details, it would be safe to say that anyone who uses My Canadian Pharmacy should definitely have severe doubts as to Alex's background in the medical industry.
Alex Polyakov was also among the most rampant mortgage spammers on the Internet in the winter of 2005 / 2006.
To date, no law enforcement entity has ever found Alex Polyakov, and they are all looking for him, including the FBI and Interpol. That such an evil individual is behind such a boldly, repeatedly spammed series of websites, and acting unhindered by any law enforcement organization is sickening in the extreme, and a definite risk to the public.
The sad reality is: MCP makes money. Several investigations into this group's technical infrastructure show that they receive constant traffic, and they process several hundred orders per day. Alex Polyakov and his criminal friends are profiting at the expense of the public. Something has to be done to stop this unscrupulous, malicious individual and his team.
Discovering Hijacked Servers
While investigating the technical infrastructure of these websites, it became necessary to do a great deal of digging into every element of how their domain names were registered, and to which IP addresses they were binding. This is a lengthy and time consuming process, but it exposes the lengths to which these criminals will go to obfuscate their operation, and hide their tracks.
Let's look at a domain spammed on 7 Feb 2007
In this example, the spamvertised domain is actually a 30mb freeweb host, since all filters are now extremely good at stopping these domains
Your best choice - http://evalution.30mb.com/
Levtiira $11.96 Propceiia $1.08 Caillis S0tf Tabs $5.72 Vaigrra Proffessoinal $4.09 Vaiggra S0tf Tabs $4.15 Amiben $2.80 Lorazpeam $1.78 Z0l0tf $1.11 Prz0ac $3.34 Paiixl $2.04 \/aillum $2.89 S0mma $1.38 Maxxaman $39.90 Lioptthin $39.96 Lipsoaffe $39.91 Cretsorr $3.81 Meirdiia $3.39
Resulting URL:
http://evalution.30mb.com/
Performs a JavaScript redirect to:
http://bridewellbee.com/?38796415
I was asked by several investigators how one can tell that the spammers are abusing and hijacking public servers. They claimed that their evidence pointed to servers owned by the spammers themselves. My assumption is that these investigators were relying on domain name evidence only. (The "WHOIS" data for a domain name.)
If we check only the whois data, and rely on only that, we will not learn anything meaningful at all about the domains or servers involved, with the only exception being that it will expose their nameserver domains. The info in the WHOIS for this domain is 100% fake:
Registrant: Icek Pankovich (BRIDEWELLBEE-COM-DOM) Sos. Mihai Bravu,No. 5 Bl. 4, Entr. 4, Apt. 9 Bucuresti, Sector 2 76101 Romania +040.0212516407 +040.0212516407 icek_pankovich@yahoo.com Domain servers in listed order: Name Server: ns1.amylaceouswer.com Name Server: ns2.unseldomdig.com Name Server: ns1.nohoevents.com
Let's focus on the web domain first. We'll get to the nameservers in a moment.
The WHOIS info claims it's located / hosted in Romania. However if we ping the domain:
PING bridewellbee.com (200.62.226.85): 56 data bytes 64 bytes from 200.62.226.85: icmp_seq=0 ttl=48 time=132.295 ms 64 bytes from 200.62.226.85: icmp_seq=1 ttl=48 time=150.043 ms
That exposes the IP address. We perform a whois on that IP:
inetnum: 200.62.226.80/29 status: reallocated owner: EJERCITO PERUANO - CGE ownerid: PE-EPCG-LACNIC responsible: EJERCITO PERUANO - CGE address: Av. Boulevard de Surco, -, S/N address: 33 - Lima - country: PE phone: +51 1 6105555 [] owner-c: COI tech-c: COI created: 20060906 changed: 20060906 inetnum-up: 200.62.224/19 nic-hdl: COI person: Core Internet e-mail: isp.gestion@TELMEX.COM address: Chinchon, 910, San Isidro address: L27 - Lima - Li country: PE phone: +5 11 6105555 [2852] created: 20021001 changed: 20040415
That turns out to be a public server located in Lima, Peru. It turns out not to be a web server, but the spammers have installed an infection on it named "tirqd" to make it mirror their content from whatever third party server they're providing it from, using a custom web server of their own creation.
The images on the bridewellbee.com domain are all hosted on a different IP address:
http://217.170.77.210:8080/p/images/weship.gif
That one is also infected with tirqd. We discover, using similar means that it's located in Panama.
Now: the name servers.
If we perform a whois on those domains you'll get - as usual - completely bogus contact and registrant data. So we do the same thing we did with the web domain name. Ping them and then whois the resulting IP addresses. We also try to gain who the authorized registrar was for these domains so we can report the abuse of their terms of service by these spammers. So far that approach has been working pretty well. (In the case of the following example, all these nameservers have been suspended, making it impossible for any of the domains they serve to resolve.)
ns1.amylaceouswer.com Registrar: Beijing Innovative Linkage Technology Ltd. IP Address: 65.43.7.170 ns2.unseldomdig.com Registrar: Dstr Acquisition VII, LLC (aka Dotster) IP Address: 210.34.0.101 ns1.nohoevents.com Registrar: Moniker / Ace Of Domains (At the time these nameservers were active, Moniker was notoriously lax about shutting any nameservers down.) IP address: 65.43.7.170 (so they're re-using a server.) 65.43.7.170 -> Northern Indian Center For History 210.34.0.101 -> Computer Center, Xiamen University in Beijing, China
Both, again, are public servers, owned by public institutions. These are infected with uirqd, a DNS server which again reports back to some unknown third party.
In total, this one, single spamvertised domain is abusing four publicly owned servers. Of course they've registered dozens of other domains as fallback, because they know that someone like myself will investigate and attempt to get them shut down.
The spammers are covering their tracks by registering bogus DNS with fake contact info, then registering web domains supported by the fake DNS registries, again: using 100% fake contact data. They appear to do this whole series of operations in an automated fashion, probably using a botnet of some sort. The whole operation is hosted on hijacked servers. They want suspicious users to only investigate the whois. Once they see that the whois is supported by dns entries, that usually stops the hunt and the user may conclude that these spammers are "untracable." If we go a step further, we uncover the fact that public servers not owned by the spammers were being hijacked for these purposes.
In addition: we noted that the spammers move the domains around several times a day. During the summer of 2006, an aggressive campaign of DNS reporting commenced, including server notifications and active monitoring of their hijacks of public servers. In all cases: The hijacked servers likely have very easy-to-guess root passwords. The root passwords on the server these spammers go after are most often one of a set of only 17 regularly used passwords, although the spammers, we discovered, perform a "brute-force" scan using upwards of 4,000 possible root passwords. After achieving the shutdown of one domain (either by complaints or by killing the infection process) the same domain was witnessed suddenly switching IP addresses. The same process was undertaken with one or more DNS domains, and the same migration was witnessed.
When the spammers ran out of IP addresses to compromise, they fell back on pre-registered domains via Yahoo's "HostingProd" small business domain registry. Complaints were sent to Yahoo and they eventually investigated and shut down the offending domains. Over time, Yahoo would take immediate action on these specific requests. It turns out that Yahoo domains were the mainstay of the MCP operation for many years before these server infections started taking place.
At a guess, several dozen hacked servers are employed by these spammers on any given day. Over the course of three months I personally logged 200 such IP addresses, and notified every single one of them. I only achieved success with two of them, who investigated and modified their root password. Most of the others just eventually stopped being abused by the spammers, though several have been re-employed in their army of hijacked web and DNS servers. One server in particular, located in Jakarta, Indonesia, has been routinely and repeatedly hijacked by these spammers since at least May of 2006.
An explanation of the tirqd infection is featured below.
The tirqd Unix infection
The spammers behind My Canadian Pharmacy have crafted a small-footprint http server which also acts as a mirroring proxy server. It's small enough that the rogue hacker wishing to take over a Unix server for the purposes of serving out an illegal website of any form, can do so rapidly, and with very little detection.
tirqd: An Indepth Description
This infection was originally called "tswapd" when we first began investigating it. It has more recently been renamed to "tirqd". They may rename it again. The reason those names were chosen is because they are similar to existing, legitimate system processes known as "swapd" and "irqd." A similar approach has been seen in numerous Windows viruses and Trojans, where they are commonly named similarly to existing Windows processes such as "svchost.exe", where they could rename to "svch0st.exe", using a zero instead of the letter "O".
Understanding what tirqd is actually doing takes a bit of explaining. Let's begin with a diagram:
A user who visits one of the My Canadian Pharmacy domains will actually be viewing content from a distant third-party IP address. The hijacked server is merely acting as a content proxy. We have seen this exploit used to act as a web host, an image host, and as a DNS server (using an alternate exploit named "uirqd".) One hijacked machine might serve all three purposes, but usually this is split up between three servers: one for each task. If you load any newly-spammed MCP website, and then view the properties of one of the images, you will usually show a site name or an IP address as the web host for the images. That machine is infected with tirqd, and its sole purpose will usually be to proxy only the images, not any PHP pages or other functional pages.
In total we tend to see the following breakdown of servers (all of these are merely examples and will likely not work in the future):
Newly-spammed domain: http://vzsfvma.coppicetrial.net/?5135498
Pinging coppicetrial.net web domain reveals IP address: 213.85.227.50
Loads images from the following ip domain: http://217.170.77.210:8080/legalrx/images/logo.gif (There may be either one or five different servers loading images to a single Bulker.biz website, and there is no fixed association between servers and domains.)
Whois on the web domain reveals four name servers:
- ns1.obtundert.com
- ns2.terkclass.com
- ns1.suffoccateter.com
- ns2.excentriccod.com
IP addresses for the four DNS servers were, respectively:
- 85.136.20.235 [Beijing Innovative, authorizing registrar]
- 63.223.11.14 [Moniker / Ace Of Domains, authorizing registrar]
- 64.94.117.200 [Dstr Acquisition VII, LLC, authorizing registrar]
- 63.223.11.14 [Beijing Innovative, authorizing registrar]
Each of those four IP addresses was infected with uirqd. Two of them turned out also to be infected with tirqd, being used as image hosts.
So far that is five distinct IP addresses being exploited just for this one domain. In total we discovered 40 distinct domain names associated with all four of these DNS domains.
We were able to discover additional compromised machines defined under the same hijacked DNS servers using a public blocklist URL:
http://rss.uribl.com/ns/excentriccod_com.html
While monitoring a hijacked server, there were several instances where the spammers were seen to attempt to log back in as root to reinstall the tirqd / uirqd exploit.
What Occurs During Installation
The nutshell description of what occurs during installation of the tirqd process is something along the lines of the following steps:
- Kill off a variety of log files and binary processes used to log any activity (Hide my tracks)
- Re-create those same log files and locations
- Run a new firewall setup so that the service can stop people from browsing this server who are trying to find out more about the illegal operation.
- Run the exploit, telling it to do one thing on port 8080, and another on 8888, with port 8888 used to contact a third-party IP address. Run it in a way that won't show its existence and / or will encrypt the incoming / outgoing data. (They implement a switch named "secret" whose purpose is not yet fully understood.)
- Remove any trace of the exploit file itself.
- Leave
This is malicious behavior, obviously. Removing log files and reinstalling a bunch of specific processes is a punishable offence. Further: hijacking a server for your own use is an international crime. But how would one prosecute such a crime? No actual files exist on the compromised server. Any trace that it was taken over has been deleted. The binary file itself does not exist: it merely remains running in RAM.
The IPTABLES settings included refusal of connections for numerous IP addresses, including full path domains for Visa and Mastercard, as well as several for Verizon. This was further confirmed when the code for the tswapd exploit itself was able to be captured, copied, unpacked and examined in more detail. It specifically refuses a connection to several IP addresses associated with Visa US domains, and several distinct Mastercard domains.
It has been further discovered that the exploit also employed a web monitoring URL which showed server activity. This has since been removed, probably due to a risk of exposure.
Investigating the IP address the exploit is told to connect to showed that it, too, was a hijacked public Unix server. Sometimes the chain would extend over several such hijacked servers, never giving away where the actual top-level command and control server was located.
More recent attempts now perform additional functionality, including stopping any remote IP address from logging in via ssh. They don't always do it but it's extremely common to see on most of these more recently exploited servers.
In literally every case, when the actual owner of the servers is alerted about this compromise, it is the first they have ever heard of it. As such a very specific set of instructions for remedying the exploit has been drafted, describing what it's doing and who is behind it. This has been mirrored on the following website:
http://pharmalert.zoomshare.com/
Some of these compromised servers have continually been used by these spammers for over a year. Repeated attempts to notify the owner, or their ISP, have resulted in no response whatsoever.
However, sometimes further information has been provided by the victims of this exploit. In two cases, vigilant system administrators have provided logging information for investigative purposes. Some administrators provided further details as to what other functions the exploit performed, or what other processes were disabled during the hijack attempt. More troubling still is that the spammers behind this exploit are now resorting to removing several crucial system processes including the shutdown, reboot and passwd services. This means the server can never be restarted or shut down, and the root password will always remain one that the spammer knows (at least until it's disconnected and a hardware restart is performed.) This is very destructive behavior, and indicates a further level of desperation on the part of the spammers. They must be gathering a great deal of data for them to be this obsessed with maintaining the compromised, hijacked servers for such a long time.
In summary: system administrators should verify that not only their root password is secure, but that remote ssh by the root user is disabled. To date we have discovered and monitored over 200 such compromised Unix servers. That's a ridiculously high number to feature such weak security.
Additionally: It appears that nobody in any official capacity is taking any action to notify these users. It falls to random individuals to discover these hijacks, and notify the owners of the infected systems. Several dozen ISP's and server admins are discovered and notified every month, often with no response whatsoever. It may eventually be necessary to resort to other measures such as blacklisting the IP addresses of the compromised servers.
History
It is thought that My Canadian Pharmacy first began being spammed in the summer of 2004. Further historical details are unknown at this time
Samples of fraud domains
Key-Systems GmbH
pxlckfxe.eu suspended yourmedicaleshop.be suspended
NAMESILO, LLC
goodcuringstore.com suspended puresulfuric.com suspended
NANJING IMPERIOSUS TECHNOLOGY CO. LTD.
mycanadian-pharmacy.com
R01-RU
bestcarequality.ru bestcuringvalue.ru bestherbalmart.ru besthotservices.ru bestmedsmart.ru bestpillmart.ru bestwelnesswebmart.ru canadiandrugsmart.ru canadianfasttrade.ru canadianherbmall.ru canadianherbsinc.ru canadianprivatesale.ru canadiantabletshop.ru canadiantabsdeal.ru curativefirstinc.ru curativehotsupply.ru curativepilleshop.ru curativesafereward.ru curingherbsservice.ru curingherbsshop.ru curingremedyshop.ru curingsmartquality.ru curingtabletbargain.ru deeayauc.ru estateinvestmenttrust.ru excellentcaredeal.ru excellentrxassist.ru excellentsecureservices.ru familydrugsvalue.ru familypillshop.ru familysafestore.ru familytabletoutlet.ru fastdrugsmarket.ru fastfastcompany.ru fastfastmall.ru fastherbseshop.ru fastherbwebmart.ru fastmedicalshop.ru fastmedicationmall.ru fastmedicationtrade.ru fastmedicinaltrade.ru fastpillspurchase.ru fastpillssupply.ru fastsafepurchase.ru firstcurativestore.ru firstherbalvalue.ru firstmedicatingmall.ru firstonlineinc.ru firstpharmacysupply.ru genericcareservices.ru genericdrugdeal.ru genericdrugsmart.ru genericdrugsoutlet.ru genericfamilyoutlet.ru genericfirstcompany.ru genericherbselement.ru genericrxwebmart.ru genericsmarteshop.ru globalfirstmall.ru globalhealthsupply.ru globalmedsoutlet.ru globaltabletelement.ru goodhealingoutlet.ru goodhotsale.ru goodonlineshop.ru goodpillswebmart.ru goodremedialassist.ru goodremedialservice.ru goodsmartassist.ru goodwelnessdeal.ru healingaidprogram.ru healingbestinc.ru healingcaresupply.ru healingherbquality.ru healinghotwebmart.ru healingpillwebmart.ru healingsafeoutlet.ru healingsmartinc.ru healingtrustedvalue.ru herbalfamilysale.ru herbalfamilyshop.ru herbalfastpurchase.ru herbalpharmvalue.ru herbalpillgroup.ru herbalpillsreward.ru herbaltrustedoutlet.ru homegenericgroup.ru homegenericreward.ru homehealingassist.ru homeherbalinc.ru homeherbseshop.ru homeherbsgroup.ru homemedicalsale.ru homesafesale.ru homewelnessmall.ru hotcurativeservice.ru hotherbsservices.ru hotmedicalmall.ru hotmedspurchase.ru hotmedsstore.ru hotonlinemart.ru hotorganiceshop.ru hotpillelement.ru hotprivategroup.ru hotrxsale.ru hrygyein.ru hrygyein.ru idalinacorrena.ru jonieblinni.ru jrfqqpoc.ru katrinageorge.ru lskkqeac.ru luckydrugshop.ru luckyherbalinc.ru luckynaturaldeal.ru luckyorganicinc.ru magiccaresale.ru magicdrugsvalue.ru magicorganicmarket.ru magicremedialinc.ru magicremedialreward.ru medicaldrugssupply.ru medicalherbsupply.ru medicalhotmall.ru medicalpillinc.ru medicalpillquality.ru medicalprivatemart.ru medicalremedysale.ru medicalsecurevalue.ru medicalsmartshop.ru medicaltableteshop.ru medicaltabsquality.ru medicaltrustedmart.ru medicatingorganicmarket.ru medicativeaiddeal.ru medicativefastmall.ru medicativesecureinc.ru medicinalaidbargain.ru medicinalaidsupply.ru medicinalhotsupply.ru medicinalpharmmall.ru medicinalrxassist.ru medicinalrxsale.ru mycanadiansupply.ru mycarereward.ru mycaresupply.ru myhealingsupply.ru myherbgroup.ru myhotwebmart.ru mymedicaresupply.ru mynaturaloutlet.ru mypharmaceuticdeal.ru myprescriptiondeal.ru mysmartdeal.ru mysupplementservice.ru mytabsreward.ru mytreatmentpurchase.ru naturalaidgroup.ru naturaldrugoutlet.ru naturaldrugsquality.ru naturalfirstvalue.ru naturalonlinesale.ru newgenericsstore.ru newherbmarket.ru newherbsservices.ru newmedicationinc.ru newmedicativeeshop.ru newpharmaceuticmall.ru newprivatesupply.ru newtreatmentreward.ru newwelnessvalue.ru onlinecareshop.ru onlinecuringgroup.ru onlinecuringmall.ru onlinedrugsdeal.ru onlinemedicareshop.ru onlinemedsinc.ru onlinepharmacyinc.ru onlinesafemarket.ru organicaidvalue.ru organicdrugselement.ru organicdrugshop.ru organicherbservices.ru organichotservices.ru organicpillstore.ru perfectgenericmall.ru perfectmedicalmart.ru perfectsafeeshop.ru pharmaceuticrxmart.ru privateaideshop.ru privategenericstore.ru privatepharmacymart.ru privatepillgroup.ru privateremedyreward.ru pureaidelement.ru purecurativedeal.ru purehealingvalue.ru purenaturalmarket.ru purenaturalreward.ru puretabssupply.ru purewelnessservice.ru remedialdrugcompany.ru remedialfastsale.ru remedialsafemarket.ru remedialsafeoutlet.ru ryauqczd.ru safecaremart.ru safedrugsvalue.ru safefastbargain.ru safemedsassist.ru safenaturalmart.ru safetabletshop.ru secureaidinvestment.ru securecanadianeshop.ru securecarequality.ru securegenericsale.ru securemedicationinc.ru secureremedyreward.ru smartcarevalue.ru smartcuringtrade.ru smarthealthbargain.ru smartherbalmart.ru smartherbsshop.ru smartnaturalstore.ru smartonlineinvestment.ru theaidbargain.ru thedrugtrade.ru thehotvalue.ru themedicinalvalue.ru thepilleshop.ru therxpurchase.ru thesafedeal.ru thewelnessshop.ru trustedcuringtrade.ru trustedfastmall.ru trustedgenericelement.ru vnznxxsj.ru yourbestassist.ru yourfastreward.ru yourgenericgroup.ru yourgenericsstore.ru yourherbsreward.ru yourherbsupply.ru yourhotprogram.ru yourhotwebmart.ru yourmedicareprogram.ru yourmedicaretrade.ru yourpillsoutlet.ru yourtabletdeal.ru yourtreatmentsale.ru ysafkpyk.ru zrscszjb.ru
How to Report this Spam
The quick answer is to use the Complainterator
The two main fronts in reporting this type of spam lie mainly in going after the websites they want the user to visit. The domains are always hosted on hacked or hijacked Unix servers. Three compromises take place with every single MCP website:
- Hijack of a web host
- Hijack of a DNS server
- Hijack of an image host
By "hijack", we mean that the criminals behind this operation target Unix or Linux servers with weak root passwords. They gain access and install one or more trojans, leaving no trace. These trojans run as parallel web hosts, DNS hosts and traffic-forwarding proxies. Often all three will run on one server, but much more frequently they spread out across numerous such hijacked computers.
As such, we recommend a four-tiered approach in reporting these abuses:
- Report the domain names to their registrar
- Report the name server domains to their respective registrars
- Report the potential hijack to the owner of the site's IP address
- Report the abuse of the image host's IP address or domain name.
An example
Spammed web domain: abcdefg.com (an example, obviously)
- Perform a whois on that domain. http://www.dnsstuff.com/tools/whois.ch?ip=abcdefg.com&email=on
- Note the active DNS servers.
- Perform a whois on the DNS servers in the same way.
- Visit the site and see where its images are hosted using View the Source. (Usually either an IP address or a Yahoo! / Hostingprod domain).
To the website's domain registrar and DNS registrars: notify them that the domain has been used in a spam run for this criminal organization. Refer them to this Wiki entry, or to web-based evidence. Ask that they investigate the domain's contact information, which will very likely be 100% fake. Request that they place zone files on Client Hold to prevent customer update, delete and transfer, and set the nameserver Address records to 0.0.0.0 so that they can no longer resolve. Be very specific about those requests.
If you get a response from the registrar, test to ensure the nameservers are no longer resolving. Quite often, registrars are unaware that the criminals behind this operation are very quick to re-use domain names. It is important to be as explicit as possible, and to make mention of the fact that these are criminals, not merely policy abusers. From a legal standpoint, no reputable company should be seen to be assisting a known criminal.
To report a Yahoo / Hostingprod domain abuse, send a similar complaint, making sure to mention that this is a My Canadian Pharmacy website, known to be operated by Bulker.biz, and possibly linked to Yambo Financial and Alex Polyakov. Send this complaint to the Yahoo / Hostingprod Abuse Email Address. Yahoo and Hostingprod have been extremely fast at shutting down all such domains when they are reported.
For more information on reporting hijacked servers, view the Hijacked host entry.
Sponsor Organization
Bulker.biz is the sponsor organization behind this type of site. They pay spammers to promote it, and they don't shut down illegal spammers.
One of bulker.biz's affiliate sponsors going by the moniker "ebulker" made the following posting on bulkerforum.biz in March of 2007 (the bulkerforum.biz website went dark in September of 2008):
http://bulkerforum.biz/viewtopic.php?t=1146
Posted: Wed Mar 14, 2007 11:00 am Post subject: Bulker.biz newsletter for February 2007. Last news: - New portal "Men's Health" is going to be launched next Monday! - "My Canadian Pharmacy" redesign will be rounded off soon. - Next popular products were added in February: norvasc, zyban, cymbalta ====== Features of Bulker.biz ========= Resemble our feautures: 1. Daily payouts for all the affiliates (or on demand) 2. We pay wires, WebMoney, and Fethard 3. Popular sites with a great choice of products and high ratio (beginning from 1:30) 4. 5% referral system 5. Free personal domains (ability to add your domains to our servers) 6. We pay probable refunds & chargebacks ourselves 7. Live support (icq, skype messenger & e-mail) 8. "Bonus Timer" program. Bonus-money for the three best affiliates EVERY DAY 9. Free geocities accounts ================ TOP Products ============================= - Viagra - Cialis Soft - Cialis + Viagra - Viagra Soft - Cialis - Ambien - Soma - HGH ================ TOP Domains =============================== - yahoo.com - aol.com - hotmail.com - comcast.net - sbcglobal.net - cox.net - earthlink.net - bellsouth.net - msn.com - gmail.com Best Regards, Bulker.Biz Team Mailto: support@bulker.biz ICQ: 333192431 Skype: BulkerSupport _________________ Bulker biz is: - 40% affiliates comission - Lot of very popular pharma products - Daily payments All you need for huge earnings! ICQ: 333192431; e-mail: support@bulker.biz
This outlines most of the brands which had been spammed prolifically by members of this affiliate program.
When Bulkerforum.biz was active, it was also hosted using the exact same type of hijacked botnet-supported servers.
Variant Site Appearances
Usual "My Canadian Pharmacy" with seasonal U.S. Independence Day ("4th of July") theme:

"My New Canadian Pharmacy"

OurMeds, RxMeds

UPDATE: In August 2013, this same operation appeared under a new design - OurMeds or OurMedications and also RxMeds or RxMedications. These have identical infrastructure code in the source, making them clearly part of the Eva Pharmacy affiliate program.
The fake addresses in OurMeds are the same or similar at http://ourmeds.org/contacts/ Main Office, with fake photoshopped building images. For example, http://ourmeds.org/images/mcp/contacts-1.jpg is also seen at http://www.xanaxdeals.com/ but labelled as Mexican Export Pharmacy, 1214 Reese St, Houston, TX 77012
OurMeds Corp. 7963 17 Avenue, Montreal, QC, H1Z 3R2, Canada ICS International Certified Stocks: OurMeds Corp. A-58, Prashant Vihar, New Delhi, 110086, India International Orders: OurMeds Int. 120 Eglinton Ave E, Toronto, ON, M4P 1E2, Canada
Read the FDA public safety warning .
Related spam operations
See: Bulker.biz





